

Sealing and verifying a Scrive document
Scrive ensures the long-term integrity and authenticity of every signed document by sealing it using advanced digital methods: PKI (PAdES) or KSI via Guardtime.
These technologies provide tamper-proofing and allow for independent verification—whether immediately after signing or many years later. PKI uses cryptographic keys to secure the document, while KSI leverages blockchain-based hashing to ensure that even the slightest change can be detected over time.
Scroll down to continue ⤵

Sealing of Scrive documents
As soon as all parties have electronically signed a document, Scrive seals the file using one of two advanced cryptographic methods: Public Key Infrastructure (PKI) or Keyless Signature Infrastructure (KSI) from Guardtime. The method applied depends on the specific scenario and requirements of the document.
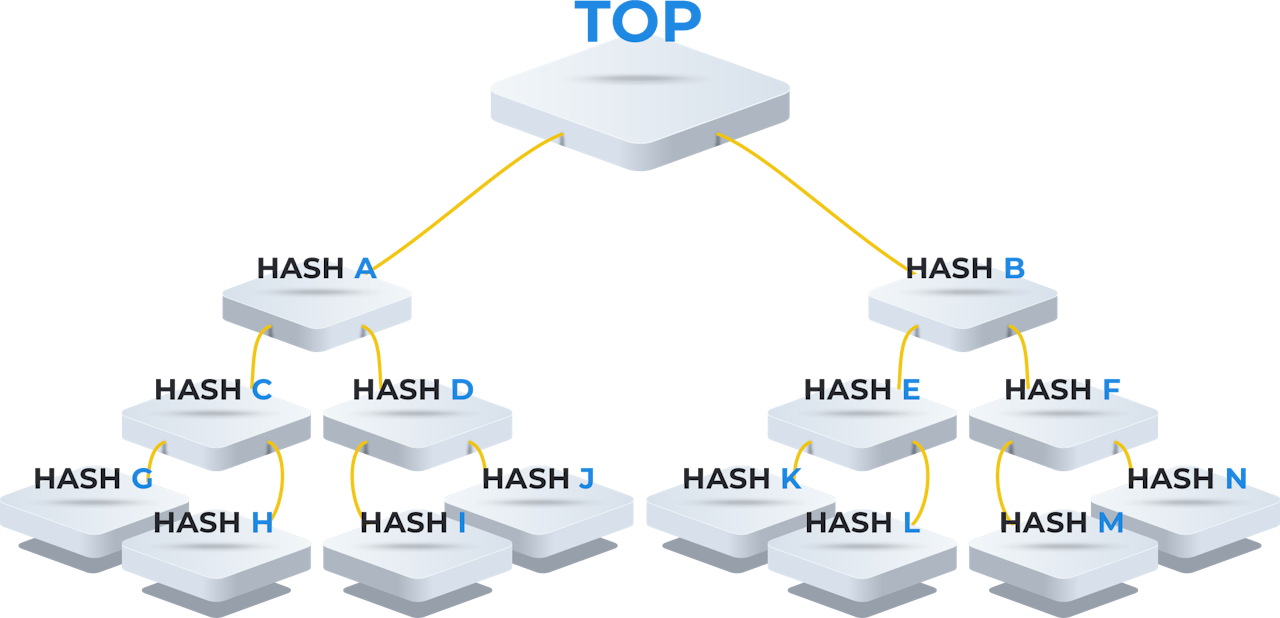
In both cases, Scrive creates a unique digital fingerprint of the file, encompassing the signed document, the Evidence Package, and any attachments. This fingerprint is a cryptographic hash—a mathematical value generated by applying a one-way function to the data. The hash is unique to the exact content of the file; even a minor change will produce a completely different result.
When KSI is used, Guardtime organizes the hash values of multiple sealed documents into a Merkle tree. This structure enables efficient and scalable verification by combining multiple hashes into one top-level hash known as the root hash. The integrity of any single document can then be verified independently, as long as the sealed document and the root hash are available and trusted.
With PKI sealing, Scrive applies a digital signature using a cryptographic key pair—one private and one public. This allows anyone with the public key to verify that the document hasn’t been tampered with since it was signed, and that it was signed by an authorized entity.
Regardless of whether PKI or KSI is used, the result is the same: your document is sealed in a way that allows you to verify its integrity at any point in the future, whether minutes or decades after signing.

Verifying a Scrive document
PKI-Sealed Documents
When a document is sealed using PKI, it receives a digital signature based on cryptographic key pairs (one private, one public). This allows anyone with the public key to independently verify the document’s authenticity and confirm that it hasn’t been altered since signing.
Verification is simple and can be done at any time using widely available tools like Adobe Acrobat Reader or other PDF signature verification software.
KSI-Sealed Documents
If your document is sealed using KSI, initial verification can be performed via Scrive or Guardtime using Scrive’s verification tool at https://scrive.com/verify.
For long-term, fully independent verification, documents must be stored in the Scrive E-archive for approximately 40 days after signing.
Here’s how the process of KSI-based independent verification works:
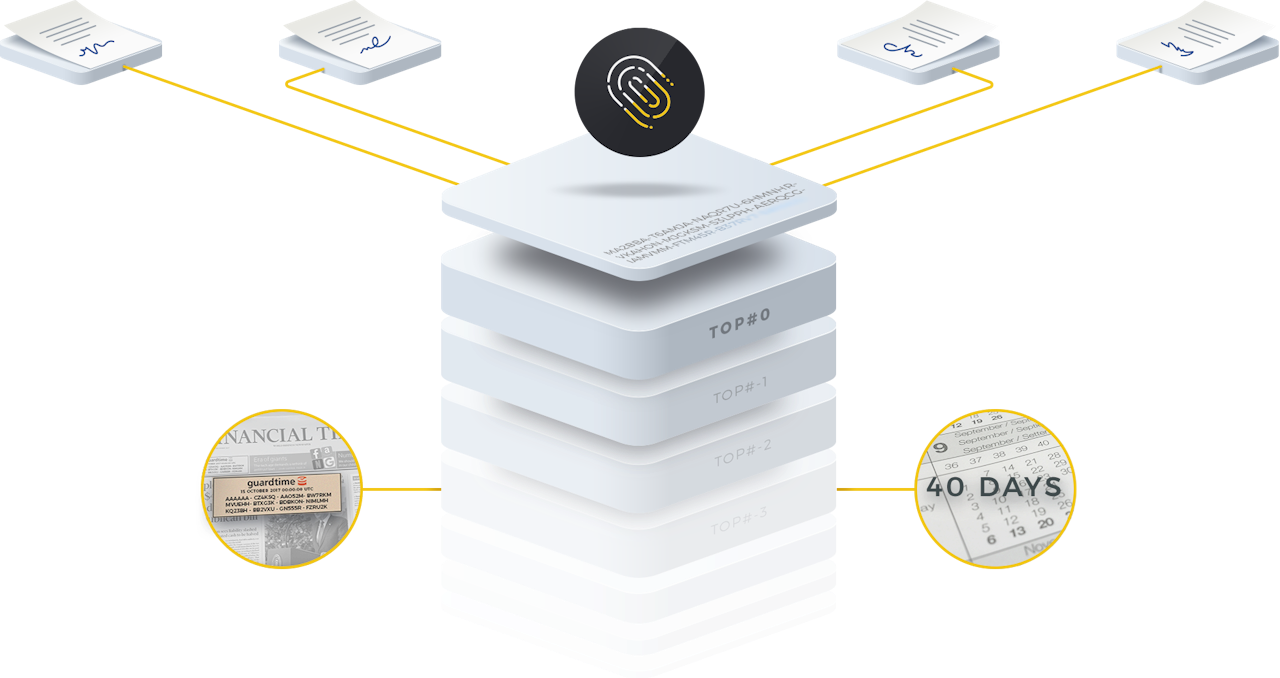
Public Hash Publication
On a recurring schedule, Guardtime publishes a top-level (root) hash representing all KSI-sealed documents from a specific period. This hash is printed in widely witnessed media, such as the Financial Times, creating a trusted public timestamp that cannot be retroactively altered by any party—including Scrive or Guardtime.Document Extension
Once the root hash is published, Scrive initiates a process called "document extension". All eligible documents stored in the Scrive E-archive during the sealing period are re-sealed with the newly published hash. This embeds the necessary verification data directly into the document.Independent, Long-Term Verification
After extension, the document can be stored anywhere—on a personal hard drive, cloud service, or external storage—and verified independently, without any reliance on Scrive or Guardtime.
If a KSI-sealed document is not stored in the E-archive during the initial 40-day window, it won’t undergo the extension process. While the seal remains secure, independent long-term verification will not be possible; you will always need to verify the document through Scrive or Guardtime.


